The File Transfer Action is used to transfer packages or application files to a remote server. The action allows for four protocols, FTP, FTPS implicit, FTPS explicit and SFTP. The action also allows for proxying the connection and setting of the accepted TLS settings when they are applicable.
Some firewalls are designed to snoop known FTP ports to work out what secondary data ports they need to allow through the firewall. With the secure transmission versions protocols FTP these firewalls are unable to workout these ports resulting in the connection failing with a data port error. A typical solution is to limit the number of data ports opened by the server and then configure the firewall to allow these ports.
Name
A friendly name for this action (will be displayed in the actions workflow area).
Enabled
Determines if this action will be run within the relevant stage.
Protocol
The action allows for the use of FTP, FTPS Explicit, FTPS Implicit, SFTP. Each providing certain capabilities and levels of security. The continua file transfer action has the following capabilities with each.
- FTP - Allow for a user login or anonymous login (by not providing a password). Note that FTP is not recommended as it is not secure.
- FTPS Implicit - Allows for connection to a host that allows both plain FTP and TLS secured connection. The action provides options for selecting the TLS version, cipher suites, and certificates which the action should accept from the server.
- FTPS Explicit - Allows for connection to a host that requires a TLS secured connection. As with FTPS Implicit the action allows configuration of the cipher suites, and accepted certificates used for the connection.
- SFTP - Allows for connection to a SSH host which also allows file transfer. In this mode the action allows setting of the key validation method.
Host
The host where the files are to be transferred. Can be the host DNS name, URL, or IP4 Address.
Port
The port that the host is listening on for the protocol selected. Standard ports for each protocol are:
- FTP: 21
- FTPS Explicit: 21
- FTPS Implicit: 990
- SFTP: 22
Some servers do use non-standard ports for a variety of reasons, please check with your provider.
Remote Folder
The folder on the remote machine to which the files will be uploaded. Note that this is based on the hosts base directory for the user. Therefore the folder selected with be a subdirectory of the home or start directory of the user login provided. This will be the folder under which all source files will be copied up. The folder structure of the source location will be replciated in the target hosts folder.
Username
The name of the user to login as on the host machine. This can be blank as some file transfer services do not require a username or password to be provided. If a username is required you will receive an error from the action stating that a login is required by the host.
Password
The matching password for the supplied username. This can be blank as some file transfer services do not require a username or password to be provided. If a password is required you will receive an error from the action stating that a login is required by the host.
Note that if the password contains a $ or % they will need to be esacped as these are identifiers for objects and variables in Continua.
Source To Transfer
The folder location of all the files and folder to be uploaded to the host folder. This is typically a workspace location such as "$Workspace$\Output\" (without the quotes). This will then supply the workspace folder (which is different for each agent and build) to the action as the location of files to upload.
Source Patterns
Each file/pattern must be entered on a new line. You can specify an exact file with its path or you can use pattern matching.
You can exclude files by prefixing the file name or pattern with a dash. e.g -*.ignore. Exclude patterns always take precedence over include patterns
More information about pattern wild cards can be found on the Ant Pattern Usage page.
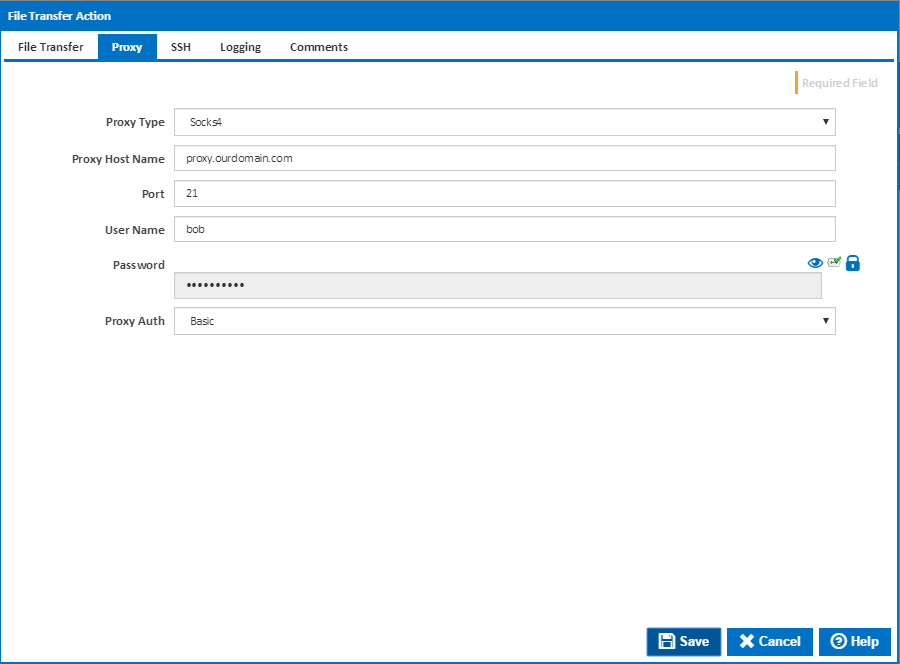
Proxy
Proxy Type
The proxy types handled by the File Transfer action are:
- Socks4
- Socks4a
- Socks5
- Http Connect
The type of proxy connection will be determined by the proxy server in use. Please talk to your network administrator as to which proxy server your company uses.
Proxy Host Name
The host name to proxy the file transfer connection through. Can be the host DNS name, URL, or IP4 Address.
Port
The port to use on the proxy for the file transfer connection. This will depend on the configuration of the proxy server in question. For this reason is highly recommend to talk to your network administrator or proxy provider as to what settings are required for your particular file transfer.
User Name
The username required to access the proxy. Some proxies require authentication to make sure your allowed to tunnel your connects through them. If the username is left blank then no username or password is used for connecting to the proxy.
Password
The password required to access the proxy. This password should match the username provided for the proxy. The password is encrypted on the system, and once entered will not be readable when editing the action.
Proxy Auth
The type of authentication the proxy server requires. The action allows for the following proxy authentication settings:
- Basic
- Ntlm
- Digest
TLS/SSL
TLS/SSL Allowed
Certificate Validation
Allowed Suites
Clear Command Channel
SSH
Key Validation