...
- FTP - Allow for a user login or anonymous login (by not providing a password). Note that FTP is not recommended as it is not secure.
- FTPS Implicit - Allows for connection to a host that allows both plain FTP and TLS secured connection. The action provides options for selecting the TLS version, cipher suites, and certificates which the action should accept from the server.
- FTPS Explicit - Allows for connection to a host that requires a TLS secured connection. As with FTPS Implicit the action allows configuration of the cipher suites, and accepted certificates used for the connection.
- SFTP - Allows for connection to a SSH host which also allows file transfer. In this mode the action allows setting of the certificate acceptance key validation method.
Host
The host where the files are to be transferred. Can be the host DNS name, URL, or IP4 Address.
...
More information about pattern wild cards can be found on the Ant Pattern Usage page.
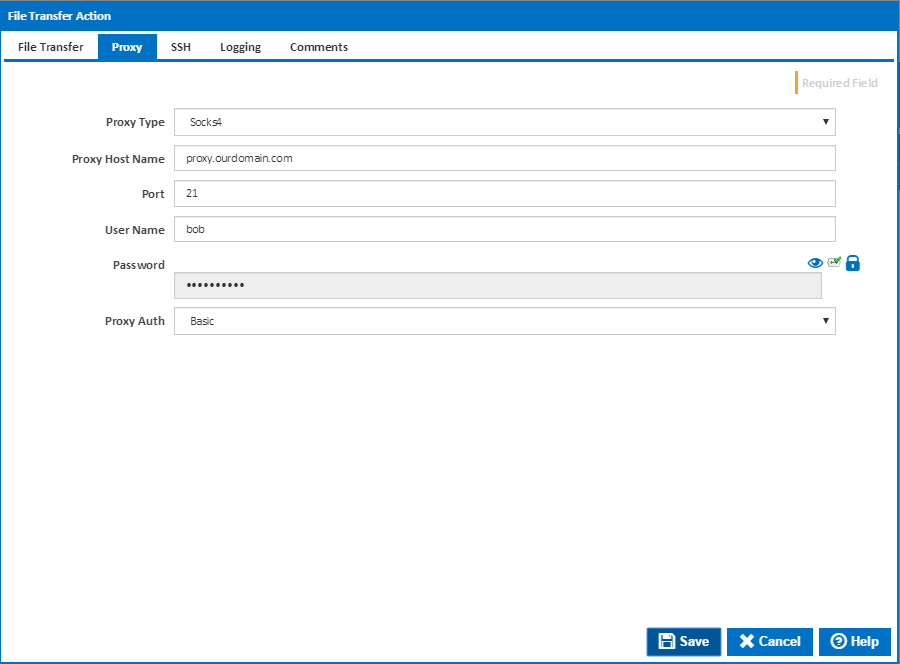
Proxy
Proxy Type
The proxy types handled by the File Transfer action are:
- Socks4
- Socks4a
- Socks5
- Http Connect
The type of proxy connection will be determined by the proxy server in use. Please talk to your network administrator as to which proxy server your company uses.
Proxy Host Name
The host name to proxy the file transfer connection through. Can be the host DNS name, URL, or IP4 Address.
Port
The port to use on the proxy for the file transfer connection. This will depend on the configuration of the proxy server in question. For this reason is highly recommend to talk to your network administrator or proxy provider as to what settings are required for your particular file transfer.
User Name
The username required to access the proxy. Some proxies require authentication to make sure your allowed to tunnel your connects through them. If the username is left blank then no username or password is used for connecting to the proxy.
Password
The password required to access the proxy. This password should match the username provided for the proxy. The password is encrypted on the system, and once entered will not be readable when editing the action.
Proxy Auth
...
The type of authentication the proxy server requires. The action allows for the following proxy authentication settings:
- Basic
- Ntlm
- Digest
TLS/SSL
TLS/SSL Allowed
Certificate Validation
...
Allowed Suites
Clear Command Channel
SSH
Key Validation